论文
网络诈骗受害过程及其影响因素
摘要
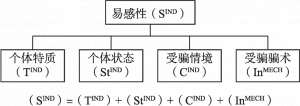
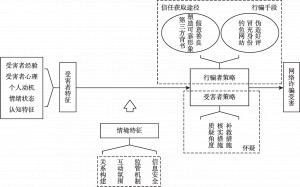
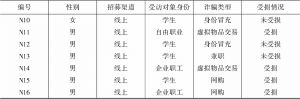
本研究通过招募选取16名网络诈骗亲历者进行访谈,经过质性分析探讨网络诈骗受害的过程及其影响因素。文本分析的结果显示,网络诈骗受害的过程可以分为三个阶段:成为目标、信任—怀疑交互、发现骗局。其中,信任—怀疑交互阶段是网络诈骗受害的关键期。网络诈骗受害涉及四个影响因素:受骗情境构成的情境特征,受害者经验和个人动机等受害者特征,信任获取途径和行骗手段等行骗者策略,以及质疑角度、核实措施、补救措施等受害者策略。网络诈骗受害是情境特征、受害者特征、行骗者策略和受害者策略协同作用的结果。
检索正文关键字
论文目录
-
一 对象与方法
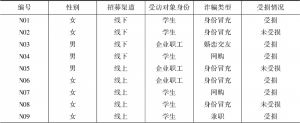
- (一)对象
- (二)方法
- 1.访谈程序
- 2.资料的处理与分析
-
二 结果
- (一)开放式编码结果
- (二)轴心式编码结果
- (三)选择性编码结果
- 三 讨论
相关文献
查看更多>>>